Thejavasea.me Leaks AIO-TLP: Safeguarding Your Data Against Major Breaches
How to Protect Yourself from the Comprehensive Data Breach of thejavasea.me Leaks AIO-TLP
In an era where data breaches are becoming increasingly sophisticated and pervasive, the recent thejavasea.me leaks aio-tlp incident stands out as a significant cybersecurity threat. This breach encompasses a wide array of sensitive information, posing severe risks to individuals and organizations. This article delves into the details of the thejavasea.me leaks aio-tlp, explores its implications, and provides actionable steps to protect against such comprehensive data breaches.
Understanding the Scope of thejavasea.me Leaks AIO-TLP
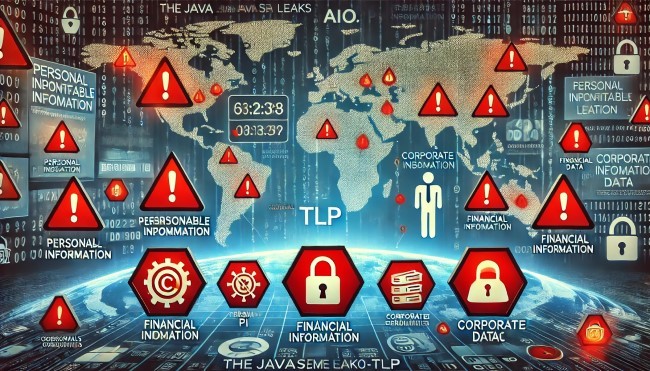
“AIO-TLP” stands for “All-In-One – Threat, Leaks, and Pwnage,” indicating a comprehensive data breach that includes various types of sensitive information. The data compromised in this breach included:
- Personal Identifiable Information (PII): Names, addresses, social security numbers, and other sensitive personal data.
- Financial Information: Credit card details, bank account numbers, and transaction records.
- Corporate Data: Proprietary information, internal communications, and strategic documents.
- Credentials: Usernames and passwords for various online services and platforms.
The Impact on Individuals
For individuals, the ramifications of thejavasea.me leaks aio-tlp are profound. The exposure of personal information can lead to identity theft, financial fraud, and a significant emotional toll due to the loss of privacy and control over personal data. The emotional and psychological impact of dealing with identity theft can be overwhelming, causing stress and anxiety that can persist long after the initial breach.
Critical Risks for Individuals:
- Identity Theft: Personal information such as social security numbers and birth dates can be used to create fraudulent accounts and engage in illegal activities.
- Financial Fraud: Compromised credit card details and bank account numbers can lead to unauthorized transactions and financial loss.
- Privacy Invasion: Exposure of sensitive information can lead to unwanted attention and misuse by malicious actors.
The Impact on Businesses
Businesses affected by thejavasea.me leaks aio-tlp face substantial risks, including financial losses, reputational damage, and operational disruptions. Companies may incur significant expenses related to breach remediation, legal penalties, and loss of business due to diminished customer trust.
Critical Risks for Businesses:
- Reputation Damage: Public disclosure of a data breach can erode customer trust and harm a company’s reputation, making it difficult to recover.
- Financial Loss: Direct financial losses from fraudulent transactions and the costs associated with breach remediation, legal penalties, and potential lawsuits.
- Operational Disruption: Leaked proprietary information can impact business operations, giving competitors an unfair advantage and leading to strategic setbacks.
Preventive Measures for Individuals
To mitigate the risks associated with data breaches like thejavasea.me leaks aio-tlp, individuals must adopt proactive cybersecurity practices:
- Use Strong, Unique Passwords: Ensure each online account has a unique and strong password. Avoid reusing passwords across multiple sites.
- Enable Two-Factor Authentication (2FA): Adding an extra layer of security by requiring a second form of verification helps protect accounts even if passwords are compromised.
- Monitor Financial Statements Regularly: Keep a close eye on bank statements and credit reports to quickly detect suspicious activity.
- Be Cautious with Personal Information: Avoid sharing sensitive personal information online and be wary of phishing attempts and suspicious emails.
Preventive Measures for Businesses
Businesses need to implement robust cybersecurity measures to protect against breaches like thejavasea.me leaks aio-tlp:
- Regular Security Audits: Conduct regular security assessments to identify and address vulnerabilities in the system.
- Employee Training: Educate employees on cybersecurity best practices and the importance of safeguarding sensitive information.
- Advanced Security Technologies: Implement advanced security solutions such as encryption, firewalls, and intrusion detection systems.
- Incident Response Planning: Develop and maintain an incident response plan to quickly and effectively manage data breaches.
The Role of Technology in Cybersecurity
Technology is crucial in enhancing cybersecurity measures and protecting against data breaches. Advanced security technologies such as artificial intelligence (AI) and machine learning (ML) are increasingly being used to detect and respond to threats in real time.
Key Technological Solutions:
- Artificial Intelligence (AI) and Machine Learning (ML): These technologies can analyze vast amounts of data to identify patterns and anomalies that may indicate a breach. AI and ML can also automate threat detection and response, improving efficiency and effectiveness.
- Encryption: Ensuring that all sensitive data is encrypted both in transit and at rest makes it more difficult for unauthorized parties to access and use the information.
- Blockchain: This technology provides additional layers of security by ensuring the integrity and immutability of data.
The Importance of Awareness and Education
Awareness and education are critical components of a successful cybersecurity strategy. This involves training employees and raising awareness among the general public. Promoting a culture of security within an organization helps to mitigate the risks associated with data breaches.
Critical Awareness and Education Strategies:
- Regular Training Sessions: Conduct regular training sessions to inform employees about the latest threats and best practices.
- Clear Communication: Provide clear and concise information about potential threats and the steps that can be taken to prevent them.
- Promote a Proactive Approach: Encourage a proactive approach to cybersecurity, emphasizing the importance of vigilance and continuous improvement.
Legal and Ethical Considerations
The thejavasea.me leaks aio-tlp incident also brings various legal and ethical considerations to light. Organizations are legally obligated to protect sensitive data and may face substantial legal consequences if they fail. Additionally, there is a moral responsibility to safeguard the privacy and security of personal and corporate information.
Key Legal and Ethical Considerations:
- Compliance with Regulations: Ensure compliance with relevant data protection regulations, such as GDPR and CCPA, to avoid legal penalties.
- Ethical Responsibility: Beyond legal obligations, organizations have an ethical duty to protect the data they collect and store.
- Transparency: Maintain transparency with customers and stakeholders about data protection practices and breach response measures.
Conclusion
The thejavasea.me leaks aio-tlp incident is a critical reminder of the importance of robust cybersecurity measures in today’s digital world. By understanding the Scope and implications of such breaches, individuals and organizations can take proactive steps to protect their data and ensure the integrity of their digital systems. Adopting best practices for cybersecurity, leveraging advanced technologies, and promoting awareness and education are essential strategies for creating a more secure digital environment.
As the digital landscape continues evolving, individuals and organizations must remain vigilant and committed to protecting sensitive information from cyber threats. By fostering a culture of security and continuous improvement, we can better prepare for and respond to future breaches, ultimately fostering a more secure and resilient digital environment.