Secure File Upload Service: Best Practices for Sensitive Data
Learn best practices for encryption, access control, 2FA, and safe large file transfers—based on OWASP standards.
The internet can be a dangerous place for sharing sensitive information. Documents such as finances, medical details, and private data can easily be stolen.
Therefore, having a reliable, secure file upload service to share files is essential. During the transfer process, ensuring your data is always protected is critical.
A secure service does not just encrypt your files. It has multi-layered security features, like strong authentication and safe storage, to protect your information.
This post will highlight file upload service features you need to consider, like security controls and encryption. We’ll also cite best practices recommended by security authorities like OWASP.
We will also discuss the best practices for securely sharing sensitive files, managing large file transfers, working around file size restrictions, and more.
Most importantly, you will learn how to encrypt your uploaded files quickly to take their security to the next level. Let’s get started, send files securely, and gain added peace of mind with advanced protection.
Key Takeaways
- Learn how secure file uploads can prevent data leaks and protect your reputation.
- Explore features like end-to-end encryption, passwords, expiration dates, and access controls that create a trustworthy uploading experience.
- Understand the best practices to share files more securely.
- Enhance the control and privacy of your documents using expiration and access restrictions.
- Implement encryption tools and techniques like AES-256 to maximize file security.
Why Are Secure File Uploads Essential?
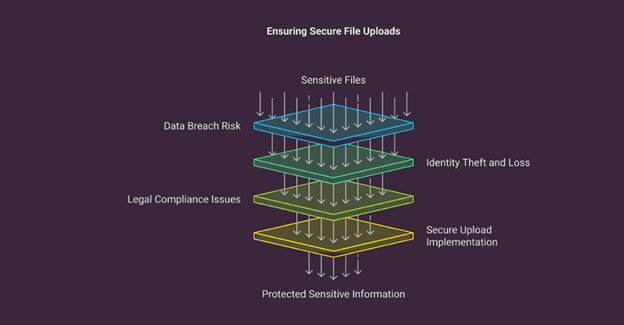
Data breaches remain a persistent threat. Hackers can quickly access personal information, business documents, and other sensitive files.
If sensitive files are leaked, the consequences can be severe. Identity theft, financial loss, and reputational damage are all potential outcomes. In some cases, legal penalties can result from non-compliance with privacy regulations such as HIPAA, GDPR, or CCPA.
Secure file uploads are a necessity for businesses. Protecting sensitive files like contracts, client information, and internal documentation is of utmost importance. Many file-uploading services offer secure plans that include encryption, user access controls, and logging.
Unauthorized access to documents can damage client relationships and the reputation of your business. In more serious cases, it can even lead to lawsuits or fines.
A secure file upload service guards against this by regulating access, encrypting files, and storing them safely. This ensures only the right individuals can view your data. Choosing a reputable, secure file uploader builds trust and compliance with industry standards.
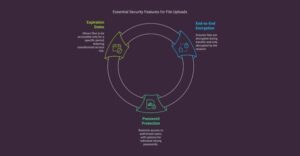
Key Security Features to Look for in a Secure File Upload Service
When selecting a file upload service, prioritize security.
1. End-to-End Encryption (E2EE)
Ensure that your files are encrypted on your device before transfer and decrypted only by the recipient. Without E2EE, files may be intercepted and read during transfer.
Example: A service using AES-256 encryption ensures that even if intercepted, the file remains unreadable without the decryption key.
2. Password Protection
Adding strong, unique passwords to each file restricts access to only authorized individuals. Some platforms allow password hints and secure sharing of the password via a separate channel.
3. Expiration Dates
Limit file availability by setting expiration dates. After the time limit, files are automatically deleted, reducing the chance of unauthorized access later.
4. Access Controls
Choose services that allow you to restrict file access to specific users or groups and implement two-factor authentication (2FA).
According to OWASP, managing file access tightly and validating user permissions helps prevent security vulnerabilities.
Best Practices for Secure File Sharing
Transferring large volumes of sensitive documents requires speed and reliability.
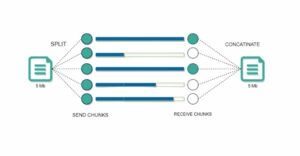
Use Chunked File Transfers
Services that support chunked uploads—splitting files into smaller parts—enhance transfer speed and resilience. This also protects against interrupted uploads and ensures consistent encryption throughout.
Enable Encryption by Default
Always use services with E2EE or encrypt files manually using tools like VeraCrypt or 7-Zip before uploading. Encryption ensures your file remains protected from upload to download.
Control File Access
Restrict access to a short list of authorized recipients. Password-protect your uploads and share the key securely via a separate medium. Add expiration dates to enforce limited-time access.
Pro Tip: Use 2FA to secure accounts associated with file-sharing platforms.
Managing File Transfers and File Size Constraints
Transferring large files doesn’t have to compromise security.
- Use services that offer chunked uploads to avoid timeouts and maintain data integrity.
- Encrypt files before transfer, especially when sharing sensitive documents.
- Store files in platforms that allow access management, audit trails, and cloud security features.
- Always set expiration dates and monitor file-sharing logs to audit activity.
- Choose vendors that support 2FA and permission-based access controls.
For secure transfers of files up to 20 GB, consider using platforms like Filestack, WeTransfer Pro, or Dropbox with encryption enabled.
Enhancing Control and Privacy
Advanced controls ensure that your file isn’t accessible beyond its intended audience.
File Expiration and Access Limits
Expiration dates automatically remove files after a defined timeframe. This is ideal for temporary or sensitive documents such as proposals, contracts, or health records.
Limit Number of Viewers
Restrict access to named users or user groups. Combine this with password protection and use secure messaging tools to distribute the access credentials.
Use 2FA for Account Access
Add a layer of protection so that even if login credentials are stolen, unauthorized access is blocked.
Example: A file protected by 2FA, a password, and an expiration date offers three critical barriers against unauthorized access.
Leveraging Encryption for Maximum Security
Encryption is the cornerstone of file security.
End-to-End Encryption (E2EE)
Only the sender and recipient can access the file’s content. Services like Tresorit, ProtonDrive, and support E2EE by default.
Use Strong Encryption Algorithms
AES-256 is the industry gold standard for encrypting sensitive data. For less critical files, AES-128 may suffice, but always evaluate the data’s sensitivity.
Manual Encryption
Before uploading, encrypt files with open-source tools like:
- VeraCrypt – ideal for encrypted volumes
- 7-Zip – for creating encrypted .zip/.7z archives
Always share decryption keys securely, using a separate communication channel.
Conclusion
Nearly every device today contains sensitive data, making secure file sharing non-negotiable. Cyber threats are real and constant. A secure file upload service can prevent breaches, identity theft, and financial loss.
When choosing a platform:
- Look for end-to-end encryption
- Require passwords and access control
- Set file expiration dates
- Use chunked transfers for large files
- Always enable two-factor authentication
A secure file upload solution doesn’t just protect your files—it protects your business, your clients, and your peace of mind.
FAQs
What is the most secure file upload service?
Choose services with end-to-end encryption, strong access controls, and regular security audits, such as Filestack, Tresorit, or Sync.com.
How do I upload a secure file?
Encrypt the file before uploading, use a platform with password protection and 2FA, and share decryption keys separately.
How can you transfer 20 GB of data online for free?
Use cloud services like WeTransfer Pro, which support large files and offer free or trial plans with security features.
What is the best site to upload files?
Top choices include Filestack, Google Drive, Dropbox, and other alternatives that support encryption, access control, and compliance with data regulations.
Editor’s Note: The guidance in this article is based on current industry standards, including OWASP and NIST guidelines. For specific security implementations, always consult a certified cybersecurity professional.